|
Contents
Summary
Agenda
Artwork Gallery
Participants
Day 1
Introduction
An Exploration of Zig-Zagging
Hider Theory
Investigating Terrorist and Smuggling Games
An Operation Perspective of Submarine Evasion Operations
An Operation Perspective of Smuggling Tactics
Day 2
Breakout Sessions
Hiding Contraband (WMD)
ASW & Military Examples
Final Summary
|
Afternoon Session
Group 1: Hiding Contraband (WMD)
Steve Basile, Rob Bentell, Jeff Cares, Bill Glenney, Tim Mertens,
Frank Tito
Download PowerPoint
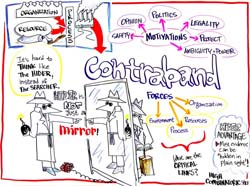
The contraband group was initially interested in the dimensions
and different axes of the contraband scenario. They began by looking
at the viewpoint of the searcher but then concentrated on the character
of the Hider. They supposed that the searcher and Hider did not
have mirror image strategies.
See enlargement
With respect to the forces and elements involved, a contraband
organization is comprised of policy makers, financiers, scientists,
technicians, deliverers, and suppliers. These are all people who
communicate with each other. They have contracts, policies, links,
and social networks with each other. The interrelationships can
be based on trust or fear among other factors.
Resources could be outwardly benign and isolated and then turn
out to be a location where chemical weapons are made or stored.
These resources may may be money, raw materials, recipe, or the
site itself, and can be in a physical or virtual location.
The scheme of producing the contraband is an arrangement of the resources and organizations involved. The contraband is the end result or product of a process.
Environmental considerations have much to do with the size of the item and the space where it will be hidden. Background noise of the environment is a factor is disguising the contraband. Familiarity of one's surroundings helps in deciding where to hide something. One also needs to recognize the neutral or unrelated activity that is occurring, as in the case of searching for the white van in DC during the sniper activities. Clutter, evasion, deception, decoy and blending in with the background are all very operative in the hiding scenario.
“What are we trying to hide?” The organization, resources, and the process or contraband are all among the things being hidden, either independently or all together. Specifically this group concentrated on undeclared WMD in a stockpile volume equivalent to a 3-car garage. The WMD would be hidden within a country while the peripherals such as resources, people and cash could be hidden globally.
Reasons for hiding may involve issues of legality where one might want to prevent sanctions or protect sovereignty. One might hide something to maintain the element of surprise. Intentions to hide would also include wanting to obscure the amount of WMD that actually exists, to protect the stockpile for later use, and to maintain its capability, capacity and readiness. World opinion may factor in for hiding purposes. One might seek sympathy for a regime while contraband remains hidden. The affect on political events and political strategy would also be motivation to keep things hidden for certain time periods.
The success factors can be shown in the process diagram below.
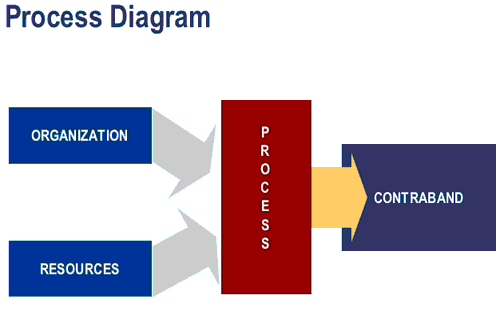
The organization can be detected. A toothpaste factory as a resource could be the place of manufacture. The question is, “what happens and what is the vulnerability involved in the process on the way to the hidden contraband?” It is hard to catch someone red-handed unless you can find the process because you may never get to the contraband. As a Hider we have to think where our advantage is. If we leave the process in the open, then we have become disadvantaged in the same way as if we hide the WMD in an accessible place.
Network strategy plays into the Hider picture. The Network Strategy
diagram shows the rations of buttons to strings and the number of
buttons connected. If I'm a Hider and am trying to hide my process,
I can have the toothpaste factory as pieces and parts of the capability,
but not have the process in view. The Hider advantage is not just
in hiding a 3-car garage somewhere in our country, but to hide major
dual-use elements oth the organization and resources in plain sight.
You can think of the same thing for drugs, Al Qaida, embezzlement
and other processes.

Many of the parts are hidden in plain sight. Links are often the things that are telling. The Hider would need an invisible (however, non-existent) thread. The Hider relies on what the searchers' capabilities, knowledge, and accessibility would be. Where not to hide the contraband is often based on where one thinks the searchers would begin to look for it.
|

