|
Contents
Summary
Agenda
Artwork Gallery
Participants
Day 1
Introduction
An Exploration of Zig-Zagging
Hider Theory
Investigating Terrorist and Smuggling Games
An Operation Perspective of Submarine Evasion Operations
An Operation Perspective of Smuggling Tactics
Day 2
Breakout Sessions
Hiding Contraband (WMD)
ASW & Military Examples
Final Summary
|
Introduction
Jeff Cares, Alidade Inc.
See Histroy of Search Theory Summary
See PowerPoint Presentation
Jeff began the day with an overview of Search Theory and the evolution
of the issues studied by the group overview the last four years,
emphasizing that this workshop would focus on “Hider” Theory.
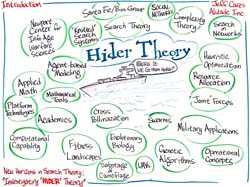
See enlargement
In addition, his presentation covered previous workshops. Jeff
explained how some in the Newport military community started back
in 1999 looking at different topics, among them complex systems.
They spent some time at the Santa Fe Institute and realized there
is a very robust non-military community out there studying Search
Theory. This gave rise to the Newport Center for Information Age
Warfare Studies and also involved the researchers at the Santa Fe
Institute and BiosGroup, Inc. There was a mix of academic and military
folks, including such luminaries as Stu Kauffman, Jose Lobo, Bill
MacReady, Wayne Hughes, Brian McCue, and Don DelBalzo.
The premise for the workshop series became this:
Search Theory, as understood by military researchers, had not
fundamentally changed in many decades, although the platforms
and operational concepts were under extraordinary transformation.
See PowerPoint Presentation
2001: From Abstraction to Application
In the first year of the Search Theory Workshop Series, academic
Search Theorists were brought together with the military to see
if the academic side could inform the military Search Theorists
and to see if both sides shared any commonalities. Academics had
only heard briefly of Koopman, upon whose work the military based
their classic Search Theory. At the end of the first conference,
the group determined that there was indeed a desire to continue
meeting.
2002: Search Theory, Invented Now
The second conference concentrated on new mathematical results
and modeling techniques. Specifically the group examined the changes in operational concepts, mathematical tools and
platform technologies.
Since the original Search Theory work was produced using the tools
of the time, Jeff posed the question, “If we were to use the tools
and methods available to us now, would we invent the same Search
Theory now as we did then?”
Guests included Josh Epstein, Fred Glover, Rob Axtell, Brian McCue,
Ralph Klingbeil, and Ray Hill, and involved agent-based modeling
approaches to Search Theory.
2003: Networked Searches, Searches in Networks
Last year, because people were building netted search systems and
databases, the workshop explored the aspects of searches using networks,
as well as searches within networks. Methods for efficient ways
of searching within large complex systems were discussed. Participants
included Dave Davis, Peter Dodd, Brian McCue, Ray Christian, and
Ray Hill.
“Hider” theory emerged as the topic of interest for this year.
The challenge became finding speakers who were experts on the topic.
We discovered that there are almost no experts in this field to
speak of, and almost no literature. In investigating Hider Theory,
Jeff listed the examples below as types of common problems such
a theory would address:
-
A ballistic missile submarine (SSBN) that
does not want to be detected while on deterrence patrol;
-
A downed pilot in enemy-controlled territory
who does not want to be found by the enemy but does want to
be rescued;
-
An embezzler who does not want to be discovered
for a long time;
-
An in-country terrorist waiting for orders
or opportunity to strike within some time duration;
-
An encrypted electronic message that is perhaps
buried within a benign or noisy transmission;
-
A pollution event—hiding who did it
and perhaps blaming someone else.
|

