|
Contents
Summary
Agenda
Artwork Gallery
Participants
Day 1
Introduction
An Exploration of Zig-Zagging
Hider Theory
Investigating Terrorist and Smuggling Games
An Operation Perspective of Submarine Evasion Operations
An Operation Perspective of Smuggling Tactics
Day 2
Breakout Sessions
Hiding Contraband (WMD)
ASW & Military Examples
Final Summary
|
Day Two: Breakout Groups
Jeff announced that the day would begin with breakout sessions
with two groups, smugglers and ASW. He prompted everyone, “until
you can begin to talk in detail about a process, you have to articulate
and describe the operational context in which the process exists.”
Before going into the breakouts he highlighted the following questions
and factors that need to be considered in the discussions.
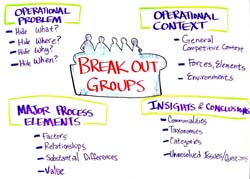
See enlargement
Operational Context
Describe the Operational Context
- General competitive context
- Forces, elements involved
- Environmental considerations
Operational Problem
Describe the specific Hider application
- Hide what?
- Hide where?
- Hide why?
- Hide when?
Major Process Elements
Hide How?
- What are the major factors that impact hider success?
- What are the relationships between these major factors?
- Are any of these substantially greater than the others?
Insights and Conclusions
|

