Afternoon
Colloquium
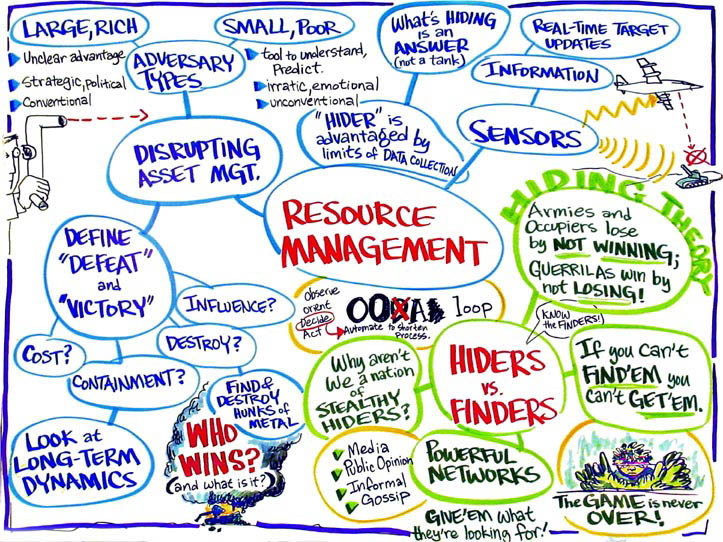
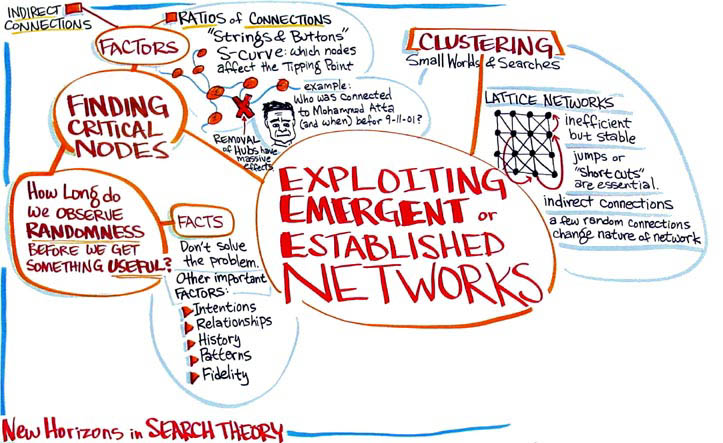
What
kinds of groupings should be looked for in emergent or established networks
(particularly those that can be exploited)?
The
general topic here is complex networks (networks with adaptable structure
and lots of overhead and obscure or irregular lengths of nodes). When
we talk about this topic from a defense perspective we are talking about
critical nodes in a process that can be exploited. A lot of networks in
the real world have these characteristics.
Click
image for enlargement
An
example of this type of network can be demonstrated in a simulation involving
buttons and strings. You start with 400 buttons in a pile. Pick up one
button and tie a string to it and place it back in the pile. Repeat the
process. Eventually buttons will beging to be tied to other buttons to
strings. When the ratio of strings to buttons reaches 0.5, you get an
amazing increase of connectivity. How can we exploit this process? Do
we add or remove nodes or links? Are there specific nodes that will make
the structure fail? If we remove 10% of the nodes will the structure fall?
At what point does the slope change?
We
can look at the linked social network of the people involved in September
11, 2001. We can see who had talked to whom and who lived with whom. When
we make a map of the connections we see that right in the middle of it
was Mohammed Atta. What if he had been eliminated as a hub?
Another
example of a dynamic network is the model that Jeff showed on the first
day of the event. This model showed the internet activity in Kosovo during
the bombing. It seemed to show some type of pattern but we do not know
what it means. It is hard to establish patterns in networks. How long
do you watch a system to extract a pattern? How much is useful? How much
should we pay attention to? How long do we observe the pattern? Where
are the lengths the same and where the nodes the same?
Having
a lot of facts does not always solve the problem. Do we deliver all the
information to the commander so he can solve the problem? Is there value
in knowing where everything is? He still can't make a decision based on
knowing where everything is. There can be more information that they need
to know. Like where have troops been? Are they on the move?
What
is the heirarchy on information needed? If the networks become flat then
how do we decide what information people need to know?
What
are the military advantages of network centric theories?
It
seems to be that with military conflict, there are those that are large
powers and those that are not. If we go to war with weaker powers, it
seems that network centric theories help us go to war cheaply and not
loose as many people. If we go to war against larger powers, we are not
sure what the value on network centric theories would be. Would this theory
work against a larger power?
We
would probably use conventional weapons against a country like China.
Most large powers seem to have agreements with other large powers to just
not fight each other.
If
we went to war with a large power there seem to be a few options: conventional
weapons, nuclear or networked. Is it a good idea to use a networked approach
against a large power?
The
Chinese response to us doing anything will be catastrophic to the United
States.
Who
is winning: the Hiders or the finders?
Hiders
always win. Alidade recently hosted a war game. There was a Red Team and
a Blue Team. The Blue Team was given an extra year of budget and a menu
of what they could buy, including advanced Sensor Systems. The Blue Team
spent all their budget on surveilance systems. The Red Team only had a
few dollars. The Red Team focused on a low-tech solution for everything
the Blue Team wanted to do, but put most resources into stealth.
The
Blue Team could have won, if they could have had their third move first.
The Blue Team believed they would have the advantage, since they had a
great sensor system. They spent their money on a "finder" system
and the Red Team spent their money on "Hider" system.
The
Blue Team believed they would dominate. The Red Team did not fire a shot.
Instead, the Red Team exploited their influence in their region, which
was their ultimate objective. The Red Team gave the Blue Team enough rope
to hang themselves with bad press and being perceived as bullies.
In
the end, there was no war. The Seekers can win initially, but the Hiders
always has the advantage.
Is
there a counter in the search area that can overcome the advantage of
the Hider?
The
network aspect is going to be the key. The network can handle the information
faster and better. The network is a new thing. The Hiders have some huge
advantages and the Seekers have to find something new. The game is never
over.
The
war game taught us that the Hiders have the advantage. The Seekers have
to play the game a different way. Instead of war, the Red Team ensured
that the Blue Team was viewed by the world as a bad guy. The key was to
attack them on a non-kinetic level. The Red Team created a mind virus
that worked against Blue. They used the Internet and the media to create
and spread the virus. Both of these technologies are are inexpensive.
Is
the United States a Hider or a Seeker? We are both. We are a Hider in
the sense that we have stealth technology and Special Forces.
We are 90% finder and 10% Hider.
The Red Team used pubilc information to gain insight into the Blue Team's
strategy. They could see what the budget was since it was public information.
The Red Team had one submarine that was operational. They spent money
to get it out of port and have it tour around the world. It was a diversion.
The Red Team was secretive about what they did with their money.
What
does winning mean?
What
does it mean to win? Is is blowing up metal? We are good at that. What
makes the Hider have an advantage? Do
we just want to know where all the pieces of metal are located? If the
other side knows our game and they will play a new game. The
real game is in the information.
Hiding
Theory
Why
don't we do next year's workshop on "Hiding Theory". What are
the problems of competing networks? Are we looking at all the possible
issues? We need to do more hiding theory. How do you hide from a distributed
network force?
In
Search Theory, things start out hidden and that is why you need to find
them. What if you use Search Theory to look more into a Hidder Theory?
If
hiding is hard, then you create decoys. The Hider has all kinds of advantages.
Do the Hider advantages have limits?
Sometimes
we are not searching for something physical and sometimes something cognitive.
Click
image for enlargement
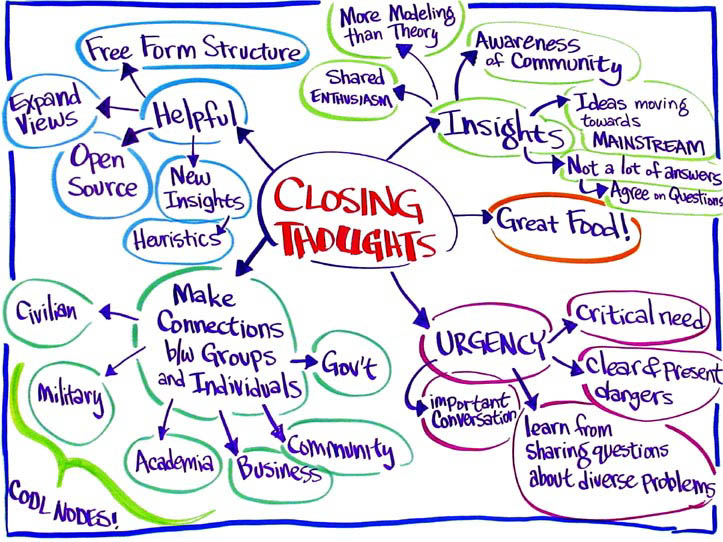
Final
Thoughts by Participants
“This
was very helpful to hear a wide variety of topics. It gave me a good perspective
of the organizations that are out there and what they are doing. I am
more aware now that the 'answer' is not out there.”
“This
event expanded my world. I feel more updated on where Search Theory stands.
I was impressed by the work being done in the modeling community.”
“I
value the update and where the community is heading.”
“I
am just starting out in this field. When I got interested in this topic,
it took me three years to get it. There are not a lot of answers. We are
still working on them.”
“This
is my first time and I did not know what to expect. I thought it would
more about "Search Theory" and we spent a lot of time on agent
based modeling. There is a lot of overlap in this field that I did not
expect. We do not have answers but we are generating a lot of questions.”
“This
was a pleasant two days. I really appreicate Jeff's enthusiasm. I enjoy
Complexity Science and being around others who are interested in this
topic.”
“I
enjoyed the Alphachimp work. The breadth of people in this room is really
great. Jeff did a great job inviting a broad experience pool. We are in
a window of opportunity. We have pull together our experiences.”
“I
want to thank all the participants. It is great to be all in one room
talking and discussing these issues.”
“I
really enjoyed this conference. I enjoyed asking people, "What problems
have you worked on?" That is the question that ties us all together.
It is gratifying to see all the presentations. I enjoyed the drawing from
Alphachimp and the value that they add. I want to thank Jeff for all his
efforts. Jeff is one of those nodes and has a lot of links to different
people. He is an ideal guy to bring this group of people together.”
“This
conference gave me a new perspective on heuristic search. It helped me
be able to explain it in a more concrete way. The [graphic facilitation]
was great.”
Click
image for enlargement
Closing
Comments
Jeff
Cares, Alidade Incorporated
I
am passionate about this topic and doing it in spite of the system's ability
to do this itself. There are real people in the field doing what they
can best do. There are people who are out there being innovative. It may
take some generation to change the system. If the system changed more
rapidly then it would not be a very stable system. I encourage you to
share the messages you heard here at this event.
Click
image for enlargement
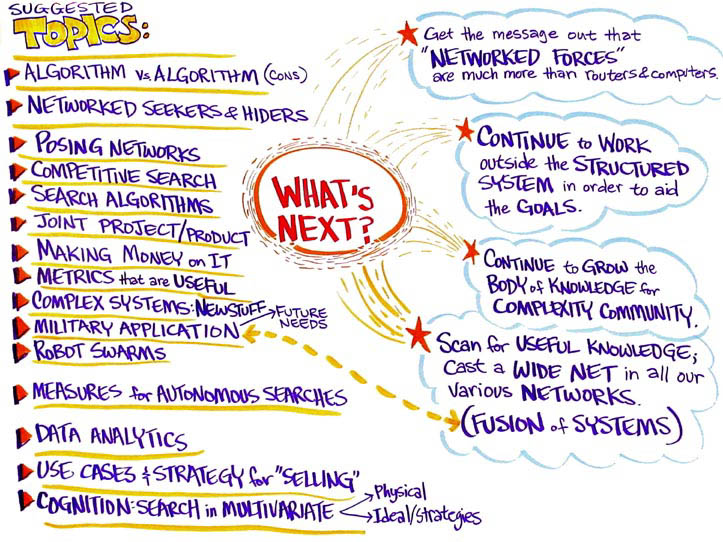
Next
year's suggested topics
-
Algorithm
vs. Algorithm
-
Networked
Seekers & Hiders
-
Fusion
Networks
-
Competitive
Search
-
Search
Algorithms
-
Joint
Project/Product
-
Making
Money in IT
-
Metrics
That Are Useful
-
Complex
Systems: New Stuff
-
Military
Application: Future Needs
-
Robot
swarms
-
Measures
for Autonomous Searches
-
Data
Analytics
-
Use
Cases & Strategy for "Selling"
-
Cognition
Search in Multivariate (physical and ideal/strategies)
|

